Turn your database
into a data vault
Mitigate the risk of data leaks by
locking down your data.
JumpWire's database gateway ensures that only authorized users and apps can access sensitive data.
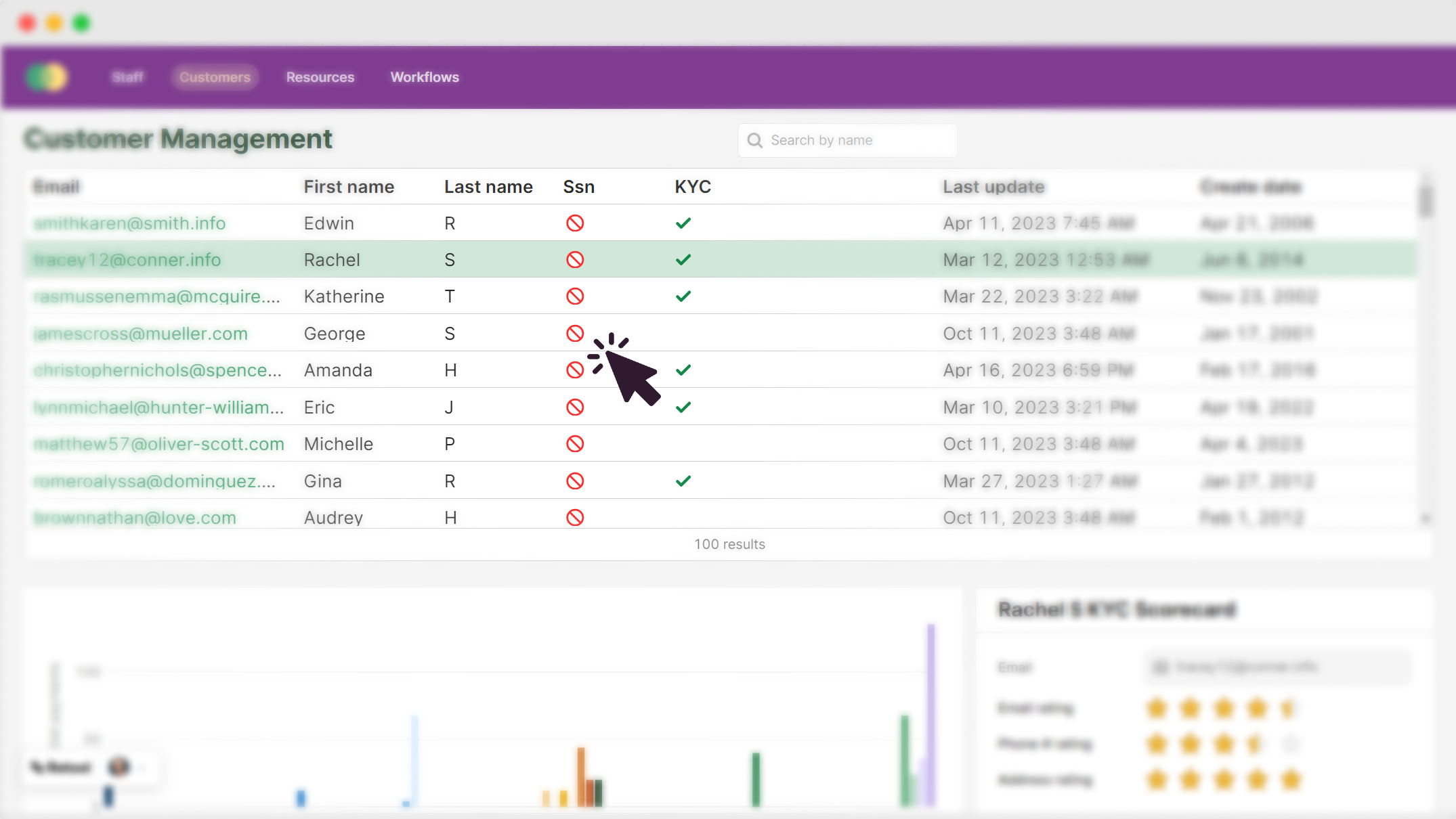
Storing data is easy. Securing it is hard.
Data breaches are growing more costly each year. The leading cause of breach is compromised credentials, which means attackers are coming from inside the house.
$9.48M
82%
26%
52%
Why JumpWire?
Stop making compromises between access to data and security.
JumpWire provides
advanced security features
that integrate seamlessly with your existing data infrastructure.
Gain full control over how data is accessed and used by every employee and application.
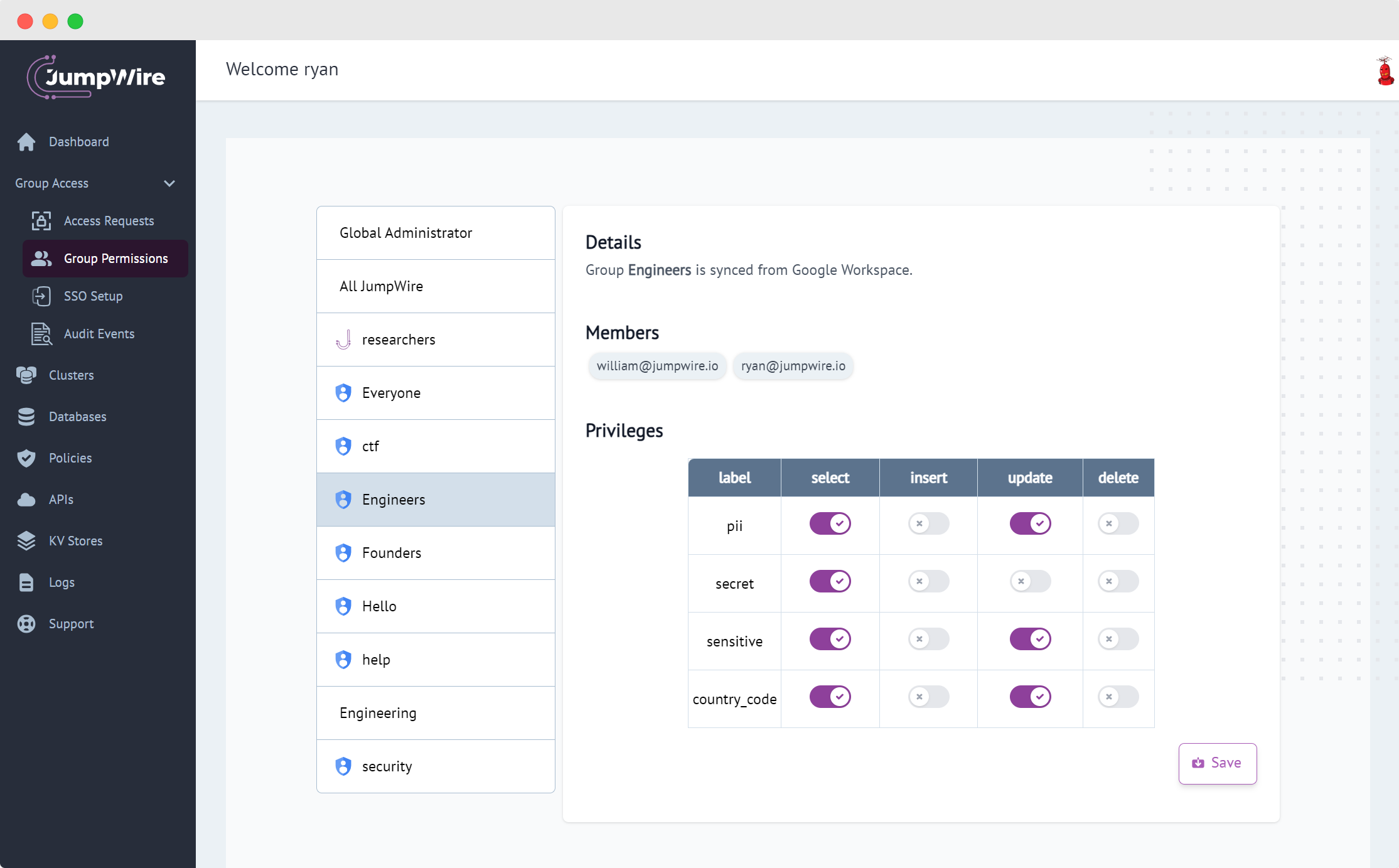
Fortifies security and access
JumpWire delivers robust capabilities for protecting your data. With features like data access approvals, encryption, audit logs, and more - JumpWire ensures your data is only available to those who need it and no one else.
Operates in your environment
JumpWire wraps your data in powerful protection right where it is - in your current databases, not 3rd-party vaults or enclaves. It operates seamlessly with existing applications and tools without the need to integrate APIs or change code.
Free and open source software
JumpWire is committed to being an open source project. Both the source code and product are developed fully in the open. This guarantees that you keep total control of your data without having to trust a 3rd party vendor.
Protect your data with JumpWire, and let your team focus on building and maintaining the applications that drive your business.
JumpWire's Capabilities
JumpWire is bringing database security into the 21st century:
- 01
Privileged access management
Replace static passwords with SSO
Map privileges to employee roles, and other attributes such as on-call status.
- 02
Content-aware rules
Operate on data confidentiality.
Policies enforce rules based on the confidentiality of data, not database schemas.
- 03
Field-level security
Protect data with field-level encryption.
Prevent specific data (like credit card numbers) from ever being read as plain text.
- 04
Enforced query filters
Ensure all queries contain filter clauses.
Provide guardrails for queries generated by third-party software and LLMs.
- 05
Query execution control
Block queries without authorization to data.
Modify data that should not be handled as plain text, by masking or tokenizing fields.
- 06
Transparent data routing
Store partial datasets in specific regions.
Join data across multiple database regions in a single request to comply with residency laws.
- 07
Complete observability
Full visibility into queries across environments.
Trace the identity of the client executing the query, as well as the confidentiality of the data being handled.
It's so easy to get started.
JumpWire has been architected to protect your data without code changes, external libraries or 3rd-party data stores. It literally deploys in 2 minutes.
Deploy
JumpWire is deployed with a single command in Docker or Helm.
docker run --name jumpwire -rm \ -e "JUMPWIRE_TOKEN=$%^#*&" \-e "JUMPWIRE_DOMAIN=localhost" \ghcr.io/extragoodlabs/jumpwireConnect
Connect the policy engine to your data stores.
Confirm
Confirm the policies generated from your schema.
- first_nameis this pii ?
- last_nameis this pii ?
- passwordis this secret ?
- emailis this sensitive ?

 Combinator '22
Combinator '22 Built by security-obsessed data people for data people everyone.
We refined JumpWire as part of the YCombinator class of winter ‘22. Now, we’re a growing team, helping anyone responsible for data security to sleep at night.
Our company Our blog1 IBM Cost of a Data Breach Report 2023
